Cybersecurity - Data Privacy - IT Trends - Innovations

Business mission to the Netherlands
At the beginning of March, the founders of the TeskaLabs, Aleš Teska (CEO) and Vladimíra Tesková (COO), participated in a business mission to the Netherlands, the topic of which was cybersecurity. The agenda included meetings with representatives of companies, educational and research organizations, discussions and sharing of experience in the fight against cybercrime or a look behind the scenes of top Dutch government and private institutions.
Published on March 15, 2023
Latest Posts

SP-Lang: Category theory in the wild
We recently encountered several interesting problems that demonstrate how seemingly abstract category theory finds its practical applications and helps us solve these problems sustainably.
Published on August 20, 2022

And the winner is...Go!
What compiled language for a backend development is the right one to move our technological stack to the next level? We've started to look around for a compiled computer language that will enable us to build microservices with higher performance. Now, don't get me wrong, we don't depart from Python at all. It is the extension of the portfolio.
Published on November 15, 2021

C-ITS: The European Commission is updating the list of the Root Certificates
23rd April 2021 marks the release of the fifth edition of the European Certificate Trust List (ECTL). This was released by the Joint Research Centre of the European Commission (EC JRC), and is used in Cooperative Intelligent Transport Systems (C-ITS). It is otherwise known as the L0 edition release, intended for use primarily in test and pilot deployments. Currently these activities are primarily European and focus on fields such as intelligent cars and road infrastructure.
press
automotive
c-its
v2x
security
Published on May 06, 2021

TeskaLabs at the ETSI 1st C-V2X Plugtest
After a succesfull ETSI C-ITS Security plugtest at November 2019, TeskaLabs participated also at the ETSI 1st C-V2X Plugtest at DEKRA Testing & Certification Malaga Location, Spain, from 2nd to 6th December 2019. C-V2X is a new standard of how vehicles communicates among each other using a cellular network.
Published on December 15, 2019

TeskaLabs at the ETSI 7th CMS Plugtest validating C-ITS security
It is our great pleasure to announce that TeskaLabs successfully participated at the ETSI 7th CMS Plugtest at Sophia Antipolis, France, from 4th to 7th November 2019. This V2X plugtest was focused on testing C-ITS cyber security, interoperability and a validation of the European trust domain.
Published on November 15, 2019

How we work at TeskaLabs
How we work at TeskaLabs. We understand that our lives are finite so we focus on things that truly matters. We build the company that builds great products.
Published on September 15, 2019

Personal Data Deindetification: Pseudonymization
Pseudonymization is a critical part of GDPR compliance although there are no explicit GDPR pseudonymization requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on July 15, 2018
Building a private cloud on AMD Ryzen and Linux Containers
At our company, we develop our own software products that we offer to our clients and often also run ourselves. So far our company has operated its IT infrastructure — about 30 virtual servers—on a public cloud, specifically on MS Azure.
Published on July 01, 2018

Personal Data Deindetification: Homomorphic encryption
Homomorphic encryption is a special type of encryption invented by IBM. Encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on June 14, 2018

Personal Data Deindetification: Data masking (or suppression)
Data masking (or suppression) represents the de fact standard of pseudonymisation. Pseudonymisation is a critical part of GDPR compliance although there are no explicit GDPR pseudonymisation requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on June 11, 2018

Personal Data Deindetification: Data Encryption
Data encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on May 16, 2018

Personal Data Deindetification: Anonymization
If you manage private data of any kind, you need to be familiar with the process of anonymization and how it can be used to keep the information you store safe from data breaches.
Published on April 16, 2018

TeskaLabs Annual Report 2017
TeskaLabs was very successful in 2017. Let’s start with numbers: TeskaLabs made a gross profit of $254,091 with before-tax earnings of $69,059. The company had positive cashflow in each month of the financial year 2017.
Published on March 16, 2018

Pseudonymization, Anonymization, Encryption ... what is the difference?
The year 2018 will, at least in Europe, be a turning point for data privacy and personal information protection. In this article, I will focus on personal data processing. I describe methods of de-identification of personal data, such as pseudonymization, anonymization, and encryption.
Published on November 28, 2017

How Productive Is a Company Retreat to Tenerife for Startups?
I would like to share with you an exciting experience that we at TeskaLabs recently had. I founded TeskaLabs three years ago, as a startup focusing on building communication and security technologies for connected products such as mobile applications and IoT devices. Over that time, my team and I have witnessed so much. We’ve been a part of the TechStars program in London and worked closely with eKasa, who have tested our business and technology to its limits.
Published on July 22, 2017

Binary distributions of OpenSSL static libraries
The official source of OpenSSL software is the OpenSSL website. One can download OpenSSL source codes archives and compile them for a given platform. The compilation work can sometimes be quite tedious, especially for exotic platforms. We, at TeskaLabs, set up this page because we frequently compile OpenSSL for various platforms for our internal purposes and this may save some time to other developers.
development
android
windows
ios
security
Published on July 20, 2017

Building High-Performance Application Servers - What You Need to Know
Using scalable and reliable software is vital for the success of any large-scale IT project. As increasing numbers of transactions are made, application infrastructure needs to stand strong and support that growth, and not be another source of problems.
Published on January 17, 2017

SeaCat and OpenSSL Heartbleed Bug
After almost two and a half year we hope that the Heartbleed remains in the past. It is not true, unfortunately. Now we have proof that a security vulnerability remains with us for a long time, maybe almost forever even when there exist patches and fixes. The Internet is a battlefield among the good, the bad, and the ugly. Who has better attacking or defending technology wins.
Published on December 20, 2016

We Know Why 85% of Mobile Apps Suck in Security. Do You?
In just the past 12 months, we’ve come across 100 mobile app projects at different phases. We’ve had conversations with more than 300 professionals active in the enterprise mobility space. We asked questions and uncovered the underlying problem that caused the current miserable state of mobile application security. It sucks. The answer doesn’t lie in technology but in us.
Published on May 19, 2016

Q&A: Mobile App Developers Asked How SeaCat Will Protect Their Apps, Backend, and the Data. Here Are the Answers
We've spent a great deal of time talking to mobile app developers to understand their approach to handling mobile application security. In this Q&A, we put together the answers to the most common questions asked by these app developers.
Published on May 07, 2015

SeaCat Starter Pack for iOS
Starter pack is SeaCat distribution package that is prepared to enable quick evaluation and understanding how SeaCat product works. Also it is a boilerplate for new mobile applications that are equipped with SeaCat.
Published on April 02, 2015

The Golden Age of Black Hats
I experienced a precious moment, discovering the cause which contributed to today's dire state of mobile application security. App developers think that if their apps do not deal with money, they should not have to care about app security. Is it true?
Published on February 24, 2015

What Can We Do as Mobile App Developers in This BYOD Era?
Today we live in a mobile environment. There are more mobile devices connected to the Internet than human beings in the world. This has given us more freedom to choose to work from anywhere, anytime and given us the flexibility to take care of other important matters.
Published on February 03, 2015

SeaCat Tutorial - Chapter 5: Using Parse.com with REST Integration (iOS)
As the market with Cloud Computing and Mobile devices is getting bigger, there is another specific option available. It's called (Mobile)Backend-As-A-Service (BAAS) and it is extremely useful in situations we want to subscribe a complex backend service (alongside the core backend solution, there is usually a lot of additional functionality and statistics) and primary focus on development of client part of mobile apps for instance.
Published on January 31, 2015

SeaCat Tutorial - Chapter 4: Using MongoDB with REST Integration (iOS)
The previous tutorial introduces several concepts and helps you understand the basic of REST API integration with iOS client written in Swift. There are several limitations, with data storage being the most important. This article provides instructions on how to work around this restriction.
Published on November 25, 2014

SeaCat tutorial - Chapter 3: Introduction to REST Integration (iOS)
The goal of this article is to extend the knowledge and develop an iOS application which is able to comunicate with REST interface provided by Node.js that we are going to create as well. A full integration with SeaCat is essential for information security of our example.
Published on October 07, 2014
SeaCat tutorial - Chapter 2: Simple Post (iOS)
The goal of this article is to create a simple iOS client which generates a simple POST Request which will be read in host written in Node.js and the output generated in the console. The whole comunication will be handled by SeaCat which help us to establish fast and secure connection among our key components.
Published on September 09, 2014

SeaCat tutorial - Chapter 1: Hello World (iOS)
This is the first practical tutorial in our tutorial series to demonstrate the strength and capabilities of SeaCat secure access solution. Our goal is to develop several sample applications and uncover the best practices you might be interested in.
Published on August 18, 2014

SeaCat Mobile Secure Gateways' Performance Test
We decided to perform this test to validate our architectural, design and implementation decisions in regards to SeaCat performance. Our goal was to build the best-in-class product using the most advanced techniques to deliver highest possible throughput yet not compromising the security of the communication. Results of the test have been fed back into our development team to improve further overall performance characteristics of the solution.
Published on July 21, 2014
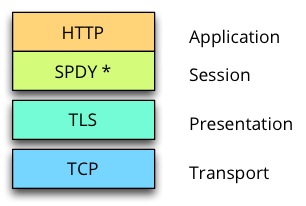
What TCP port to use with SeaCat?
SeaCat requires to specify one TCP port that is eventually used for client-gateway communication. Clients connect to this port to establish TLS channel that is used to exchange requests and related responses. SPDY-based communication protocol is used for traffic in this channel.
Published on May 23, 2014
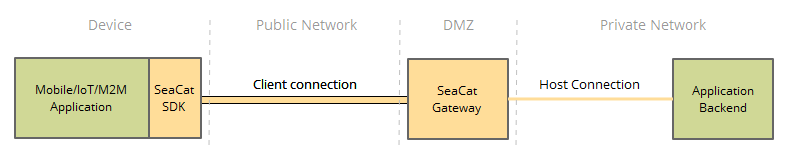
SeaCat Mobile Secure Gateway Architecture
SeaCat Mobile Secure Gateway is built using the SeaCat Application Security Platform. It provides strong protection against multiple types of cyberattacks by securing all application components, including the mobile application, network paths, which present an entry point to the enterprise network and application’s backend servers. It reduces an administrator's workload with easy PKI administration of distributed large-scale mobile applications. SeaCat Security Platform has been carefully designed to be flexible, fast, and highly secure.
Published on May 18, 2014