What TCP port to use with SeaCat
Introduction
SeaCat requires to specify one TCP port that is eventually used for client-gateway communication. Clients connect to this port to establish TLS channel that is used to exchange requests and related responses. SPDY-based communication protocol is used for traffic in this channel.

SeaCat: Protocol stack
TCP ports reachability
Google performed investigation during WebSocket implementation (late 2009) that showed surprising facts about success rate of client-to-server connections:
- HTTP port 80: 67%
- Custom TCP port (61985): 86%
- HTTPS port 443: 95%
The reason for low HTTP score is that the Internet is today full of proxies and firewalls that are configured to be transparent to HTTP traffic. However, non-HTTP traffic doesn't successfully pass them. Detailed reasoning can be found here: SPDY Essentials presentation from Google at approx. 18th minute of the video.
443 or custom port
SeaCat communication protocol is up to Session layer compatible with HTTPS protocol stack, HTTPS client that connects to SeaCat gateway is politely rejected with no harm on both sides. SeaCat traffic is indistinguishable from HTTPS traffic for intermediates on the network path, and,therefore, it shares the same success rate of connections. For these reasons TCP port 443 is recommended choice for SeaCat.
If for whatever reason you cannot use this port, use any TCP port above 1024 (non-reserved ports). You will likely got little bit worst connection success rate but still useful for practical deployments in common network scenarios.
Need help?
Do you want to review your SeaCat-related design proposal?
Do you have a question we didn’t cover?
Do you want to give some feedback?
Feel free to contact us support@teskalabs.com.
Most Recent Articles
You Might Be Interested in Reading These Articles

SeaCat tutorial - Chapter 3: Introduction to REST Integration (iOS)
The goal of this article is to extend the knowledge and develop an iOS application which is able to comunicate with REST interface provided by Node.js that we are going to create as well. A full integration with SeaCat is essential for information security of our example.
Published on October 07, 2014

SP-Lang: Category theory in the wild
We recently encountered several interesting problems that demonstrate how seemingly abstract category theory finds its practical applications and helps us solve these problems sustainably.
Published on August 20, 2022
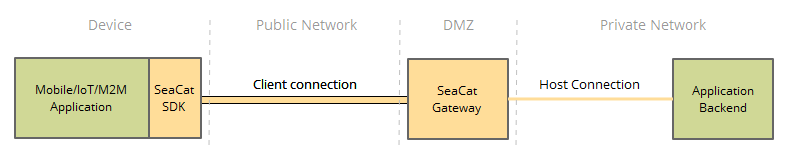
SeaCat Mobile Secure Gateway Architecture
SeaCat Mobile Secure Gateway is built using the SeaCat Application Security Platform. It provides strong protection against multiple types of cyberattacks by securing all application components, including the mobile application, network paths, which present an entry point to the enterprise network and application’s backend servers. It reduces an administrator's workload with easy PKI administration of distributed large-scale mobile applications. SeaCat Security Platform has been carefully designed to be flexible, fast, and highly secure.
Published on May 18, 2014
