Cybersecurity - Data Privacy - IT Trends - Innovations

Log management for absolute beginners
New to log management and cybersecurity? Or, maybe you're already a pro, but you're looking for a way to explain log management to someone who is? Either way, you're in the right place.
Published on April 15, 2024

A beginner-friendly intro to the Correlator for effective cybersecurity detection
At TeskaLabs, we know that a cybersecurity system is only as effective as its ability to detect threats. That's why we developed a powerful tool that will prove essential in your arsenal: the Correlator.
Published on March 15, 2024

Inotify in ASAB Library
From blocking read challenge, ctypes and bitmasks to a solution that enables the ASAB framework to react to changes in the file system in real time.
Published on August 15, 2023
From State Machine to Stateless Microservice
In my last blog post, I wrote about implementing a state machine inside a microservice I call Remote Control that will automate deployments of our products and monitor the cluster. Here I would like to describe how all this was wrong and why I had to rewrite the code completely.
Published on February 15, 2023
Entangled ways of product development in the area of cybersecurity #3 - LogMan.io
At that time I lived in Prague for a short time, which is not a very friendly place to live, but it allowed me to go to the office almost every day. A bigger surprise awaited Vlaďka and Aleš when I told them that I was going to move to a house almost eighty kilometres from the office and that I would need to be mainly at the home office.
Published on January 15, 2023
Entangled ways of product development in the area of cybersecurity #2 - BitSwan
After successfully completing my engineering degree, I finally started working full-time at TeskaLabs just as I initially promised. In addition to data from the world of telecommunications, we started to learn data from the world of logistics in BitSwan, which of course required being able to calculate the cost of transporting some cargo from point A to point B.
Published on December 15, 2022
Entangled ways of product development in the area of cybersecurity #1 - Asynchronous or parallel?
I started working at TeskaLabs at the beginning of autumn 2017 as a student at the Faculty of Information Technology of CTU. In the job advertisement, I was particularly interested in the fact that it is a small, product-based company that does not focus on just one technology or one programming language.
Published on November 15, 2022
State machine miracle
How I learned what a finite state machine is and that good design is an essential part of programming.
Published on October 15, 2022

Log Management: Pre-implementation analysis
Pre-implementation analysis is a preparatory phase on the way to deploying a functional cybersecurity management system, i.e. TeskaLabs SIEM and security event management, Log Management. It is an integral and essential part of the entire implementation process, as it helps uncover any potential risks that may arise when deploying the mentioned SIEM and log management tools.
Published on September 15, 2022

SP-Lang: Category theory in the wild
We recently encountered several interesting problems that demonstrate how seemingly abstract category theory finds its practical applications and helps us solve these problems sustainably.
Published on August 20, 2022

Engaged with ASAB
About microservices, coroutines, failures and enthusiasm. And most of all, about ASAB. ASAB is the first thing that probably every newcomer to TeskaLabs gets fond of.
Published on June 15, 2022
Don't worry, ASAB and the universe can be fixed
How do my first sprints in TeskaLabs look like? Sheer desperation quickly turns into feelings of illumination and euphoria. And back. I've also made a few new friends and learned a thing or two about flushing metrics. The digital adventure begins.
Published on February 15, 2022

And the winner is...Go!
What compiled language for a backend development is the right one to move our technological stack to the next level? We've started to look around for a compiled computer language that will enable us to build microservices with higher performance. Now, don't get me wrong, we don't depart from Python at all. It is the extension of the portfolio.
Published on November 15, 2021
Building a private cloud on AMD Ryzen and Linux Containers
At our company, we develop our own software products that we offer to our clients and often also run ourselves. So far our company has operated its IT infrastructure — about 30 virtual servers—on a public cloud, specifically on MS Azure.
Published on July 01, 2018

Building High-Performance Application Servers - What You Need to Know
Using scalable and reliable software is vital for the success of any large-scale IT project. As increasing numbers of transactions are made, application infrastructure needs to stand strong and support that growth, and not be another source of problems.
Published on January 17, 2017

What Is Mobile Application Containerization or Wrapper, and Why It Needs to Go?
Containerization is an alternative for full machine virtualization. You probably know well-known containerization technology from Docker or Rocket. However, this article addresses the pros and cons of mobile “containerization” or wrapper used to isolate the mobile app from the mobile operating system or other applications installed on the same device. These type of “containerization” work in a different way.
Published on September 27, 2016

Is There A Network Protocol for Your Mobile Apps That Offers A Higher Security Level While Consuming Less Bandwidth Than HTTPS? Yes, There Is
For mobile apps or websites that don’t have logins, forms or features to extract data, you don’t need secure access. For banking websites, mobile apps and mobile banking services, without a doubt, secure communication is a must. But nothing is ever black and white.
Published on September 13, 2016

The Outrageous Cost of HTTPS - Why?
Mobile applications use HTTP communication between the application backend and the clients. Because of the demand for higher level of security, IT people implement HTTPS by setting up certificates issued by LetsEncrypt Certification Authority in their application backend server. The shift between non secure HTTP connections to HTTPS connections leads to a significant increase of amount of data being transferred from/to the clients. How is this possible?
Published on June 14, 2016

Q&A: Mobile App Developers Asked How SeaCat Will Protect Their Apps, Backend, and the Data. Here Are the Answers
We've spent a great deal of time talking to mobile app developers to understand their approach to handling mobile application security. In this Q&A, we put together the answers to the most common questions asked by these app developers.
Published on May 07, 2015

SeaCat Starter Pack for iOS
Starter pack is SeaCat distribution package that is prepared to enable quick evaluation and understanding how SeaCat product works. Also it is a boilerplate for new mobile applications that are equipped with SeaCat.
Published on April 02, 2015

SeaCat Tutorial - Chapter 5: Using Parse.com with REST Integration (iOS)
As the market with Cloud Computing and Mobile devices is getting bigger, there is another specific option available. It's called (Mobile)Backend-As-A-Service (BAAS) and it is extremely useful in situations we want to subscribe a complex backend service (alongside the core backend solution, there is usually a lot of additional functionality and statistics) and primary focus on development of client part of mobile apps for instance.
Published on January 31, 2015

Save the Day and Do the Impossible - Business Intelligence Community Stays Tuned
Let us share with you fresh news from the SeaCat kitchen. A few weeks ago we had a workshop with one potential customer who was currently working on a mobile application which should access Oracle Business Intelligence (BI) suite, basically Oracle Business Intelligence Mobile HD based solution. We piloted Oracle BI SDK & SeaCat integration.
Published on November 30, 2014

What’s The Difference Between Seacat and VPN?
One of the most common questions people asked us is if SeaCat some kind of a VPN? It's not. Virtual Private Network (VPN) extends a private network across a public network, providing secure connectivity from/to a mobile device. Every application on this device, thus now has access to the private network through the channel opened by VPN. This is safe up to a certain level because it is almost impossible to ensure the integrity of every application on the devices. Especially now when there are apps for everything, and users can download them from Google Play and the Apple store.
Published on November 25, 2014

SeaCat Tutorial - Chapter 4: Using MongoDB with REST Integration (iOS)
The previous tutorial introduces several concepts and helps you understand the basic of REST API integration with iOS client written in Swift. There are several limitations, with data storage being the most important. This article provides instructions on how to work around this restriction.
Published on November 25, 2014

SeaCat tutorial - Chapter 3: Introduction to REST Integration (iOS)
The goal of this article is to extend the knowledge and develop an iOS application which is able to comunicate with REST interface provided by Node.js that we are going to create as well. A full integration with SeaCat is essential for information security of our example.
Published on October 07, 2014
SeaCat tutorial - Chapter 2: Simple Post (iOS)
The goal of this article is to create a simple iOS client which generates a simple POST Request which will be read in host written in Node.js and the output generated in the console. The whole comunication will be handled by SeaCat which help us to establish fast and secure connection among our key components.
Published on September 09, 2014

SeaCat tutorial - Chapter 1: Hello World (iOS)
This is the first practical tutorial in our tutorial series to demonstrate the strength and capabilities of SeaCat secure access solution. Our goal is to develop several sample applications and uncover the best practices you might be interested in.
Published on August 18, 2014

SeaCat FREE trial
In order to help you to evaluate and use our product we have prepared an trial version that is freely available for download. Trial version is limited to emulator/simulator only, you cannot use that on a real device. There is however no expiration date of a trial, so feel free to use it for any amount of time you need for the evaluation or even an actual development.
Published on August 17, 2014

SeaCat Mobile Secure Gateways' Performance Test
We decided to perform this test to validate our architectural, design and implementation decisions in regards to SeaCat performance. Our goal was to build the best-in-class product using the most advanced techniques to deliver highest possible throughput yet not compromising the security of the communication. Results of the test have been fed back into our development team to improve further overall performance characteristics of the solution.
Published on July 21, 2014
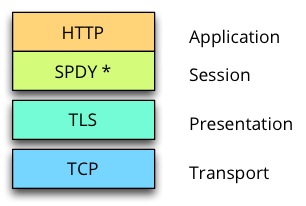
What TCP port to use with SeaCat?
SeaCat requires to specify one TCP port that is eventually used for client-gateway communication. Clients connect to this port to establish TLS channel that is used to exchange requests and related responses. SPDY-based communication protocol is used for traffic in this channel.
Published on May 23, 2014
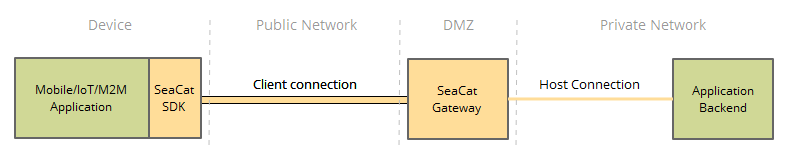
SeaCat Mobile Secure Gateway Architecture
SeaCat Mobile Secure Gateway is built using the SeaCat Application Security Platform. It provides strong protection against multiple types of cyberattacks by securing all application components, including the mobile application, network paths, which present an entry point to the enterprise network and application’s backend servers. It reduces an administrator's workload with easy PKI administration of distributed large-scale mobile applications. SeaCat Security Platform has been carefully designed to be flexible, fast, and highly secure.
Published on May 18, 2014
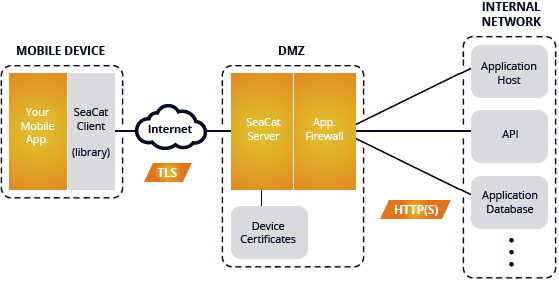
Software architect's point of view: Why use SeaCat
I've recently received an interesting question from one software architect: Why should he consider embedding SeaCat in his intended mobile application? This turned into a detailed discussion and I realised that not every benefit of SeaCat technology is apparent at first glance. Let me discuss the most common challenges of a software developer in the area of secure mobile communication and the way SeaCat helps to resolve them. The initial impulse for building SeaCat was actually out of frustration of repeating development challenges linked with implementation of secure mobile application communication. So let's talk about the most common challenges and how SeaCat address them.
Published on April 16, 2014

SeaCat trial for iOS on Mac OSX
This blog entry is meant to help you to start using SeaCat component on your Xcode iOS development environment. It contains instructions how to install and configure SeaCat gateway and how to integrate SeaCat client into your iOS application. SeaCat gateway is a secure gate to the restricted network. It allows access only to selected HTTP hosts and prevents exposure of others. It also secures communication with SeaCat clients that are typically in the Internet. SeaCat client becomes part of said mobile application and provides secured channel to SeaCat gateway and to target hosts in the restricted network. It ensures mutual security of the connection and transferred data.
Published on March 14, 2014