SeaCat Starter Pack (iOS)
Foreword
SeaCat starter pack is a distribution package, prepared to allow quick evaluation and understanding of how SeaCat product works. It is also a boilerplate for new mobile applications equipped with SeaCat.
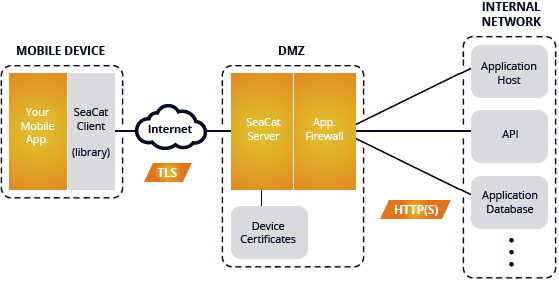
The package consists of a simple iOS application, pre-integrated with SeaCat framework (SDK) and pre-configured gateway. Beside configuration, the gateway contains a simple CSR utility that allows the gateway to approve newly connected users either automatically or from the command-line.
SeaCat license is pre-installed in the starter pack.
Users can start building their mobile application based on the code in the starter pack or use it purely for evaluation or educational purposes.
To start with SeaCat starter pack, for those who have requested the pack, you should receive an email with download links. If this is not the case, please contact us at support@teskalabs.com.
( If you want a similar starter pack, please send an email to above address with "Request for SeaCat Starter Pack" in the subject line. We will follow up with you immediately. )
Instructions
- Download and unpack "SeaCat Gateway Starter pack" using the link from our email.
- Open 'Terminal' application and go to 'seacat' directory that has been created in previous step.
- Launch SeaCat gateway by './run.sh' script:

- Download and unpack "SeaCat iOS Starter pack" using the link from our email.
- Start Xcode and open the project file that has been unpacked in the previous step.
-
Run mobile application in iPhone simulator:

At this point, the mobile app waits for Certificate Signing Request approval at the gateway side.
This process is typically integrated with a backend of the mobile application. However, we will manually approve CSR using seacat-csr utility. -
Open a new session of 'Terminal' and go to the folder where you unpacked "SeaCat Gateway Starter pack".
- Run './csr.sh' command - you should be asked to approve one CSR, press 'y' + ENTER:

- Mobile application progresses to its main window and displays the result of HTTP call.
Gateway configuration
The initial gateway network location is set to localhost (127.0.0.1) port 7443 (TCP).
Please let us know if you want a different setup by sending an email to support@teskalabs.com, please don't forget to include your application bundle ID.
Configuration of SeaCat gateway can be found at seacat/etc/seacat.conf
There are two hosts pre-configured in SeaCat gateway:
- localhost.seacat points to http://localhost/
- evalhost.seacat points to http://eval.teskalabs.com/
Client certificates are stored in seacat/var/cert directories.
You can freely investigate details of these certificates using standard tools. By physically removing the certificate file, you remove a given client (mobile app instance) from the whitelist, and this client will lose access to SeaCat gateway. In that case, the Seacat starter pack application will automatically generate and submit a new CSR.
License remarks
There are no limitations in terms of number of devices, users whatsoever. However, there is an expiration time set in evaluation license.
The license is bound to one specific application id (bundle id on Apple iOS platform).
The license can be used both in a simulator and on a real device.
Users are prohibited and unauthorized to resell or pass this license to third parties.
Reach out to us via email or follow us on Twitter @TeskaLabs for additional updates.
Most Recent Articles
You Might Be Interested in Reading These Articles
Software architect's point of view: Why use SeaCat
I've recently received an interesting question from one software architect: Why should he consider embedding SeaCat in his intended mobile application? This turned into a detailed discussion and I realised that not every benefit of SeaCat technology is apparent at first glance. Let me discuss the most common challenges of a software developer in the area of secure mobile communication and the way SeaCat helps to resolve them. The initial impulse for building SeaCat was actually out of frustration of repeating development challenges linked with implementation of secure mobile application communication. So let's talk about the most common challenges and how SeaCat address them.
Published on April 16, 2014

And the winner is...Go!
What compiled language for a backend development is the right one to move our technological stack to the next level? We've started to look around for a compiled computer language that will enable us to build microservices with higher performance. Now, don't get me wrong, we don't depart from Python at all. It is the extension of the portfolio.
Published on November 15, 2021
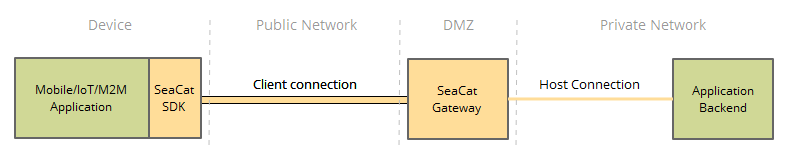
SeaCat Mobile Secure Gateway Architecture
SeaCat Mobile Secure Gateway is built using the SeaCat Application Security Platform. It provides strong protection against multiple types of cyberattacks by securing all application components, including the mobile application, network paths, which present an entry point to the enterprise network and application’s backend servers. It reduces an administrator's workload with easy PKI administration of distributed large-scale mobile applications. SeaCat Security Platform has been carefully designed to be flexible, fast, and highly secure.
Published on May 18, 2014
