Cybersecurity - Data Privacy - IT Trends - Innovations

Building the Correlator #2: Window architecture
In the previous article, I described what the window correlator is good for, analyzing long series of data to gather security incidents and produce alerts. I also discussed the memory issue that comes with storing long series of data composed of events, which come to the application at a frequency of tens of thousands of events per second. The proposed solution is to store only relevant parts of the series, here called segments, in memory. Now, we'll take a look at the segments in more detail, so we know exactly what structures they are composed of.
Published on June 15, 2024

Building the Correlator #1: Analyzing long series of cybersecurity data with window correlation
In a cybersecurity system, there are usually tens of thousands of messages transmitted every second, each containing information about user behavior, device status, connection attempts, and other activities performed in a network infrastructure. These messages are called logs, and they are produced not only by the servers themselves, but by all kinds of applications running on those servers, as well as network devices such as firewalls.
Published on May 15, 2024

Inotify in ASAB Library
From blocking read challenge, ctypes and bitmasks to a solution that enables the ASAB framework to react to changes in the file system in real time.
Published on August 15, 2023
From State Machine to Stateless Microservice
In my last blog post, I wrote about implementing a state machine inside a microservice I call Remote Control that will automate deployments of our products and monitor the cluster. Here I would like to describe how all this was wrong and why I had to rewrite the code completely.
Published on February 15, 2023
Entangled ways of product development in the area of cybersecurity #3 - LogMan.io
At that time I lived in Prague for a short time, which is not a very friendly place to live, but it allowed me to go to the office almost every day. A bigger surprise awaited Vlaďka and Aleš when I told them that I was going to move to a house almost eighty kilometres from the office and that I would need to be mainly at the home office.
Published on January 15, 2023
Entangled ways of product development in the area of cybersecurity #2 - BitSwan
After successfully completing my engineering degree, I finally started working full-time at TeskaLabs just as I initially promised. In addition to data from the world of telecommunications, we started to learn data from the world of logistics in BitSwan, which of course required being able to calculate the cost of transporting some cargo from point A to point B.
Published on December 15, 2022
Entangled ways of product development in the area of cybersecurity #1 - Asynchronous or parallel?
I started working at TeskaLabs at the beginning of autumn 2017 as a student at the Faculty of Information Technology of CTU. In the job advertisement, I was particularly interested in the fact that it is a small, product-based company that does not focus on just one technology or one programming language.
Published on November 15, 2022
State machine miracle
How I learned what a finite state machine is and that good design is an essential part of programming.
Published on October 15, 2022

Engaged with ASAB
About microservices, coroutines, failures and enthusiasm. And most of all, about ASAB. ASAB is the first thing that probably every newcomer to TeskaLabs gets fond of.
Published on June 15, 2022
Don't worry, ASAB and the universe can be fixed
How do my first sprints in TeskaLabs look like? Sheer desperation quickly turns into feelings of illumination and euphoria. And back. I've also made a few new friends and learned a thing or two about flushing metrics. The digital adventure begins.
Published on February 15, 2022

And the winner is...Go!
What compiled language for a backend development is the right one to move our technological stack to the next level? We've started to look around for a compiled computer language that will enable us to build microservices with higher performance. Now, don't get me wrong, we don't depart from Python at all. It is the extension of the portfolio.
Published on November 15, 2021

Asynchronous Server App Boilerplate Video Tutorial
Asynchronous Server App Boilerplate (or ASAB for short) is a microservice platform for Python 3.5+ and asyncio. The aim of ASAB is to minimize the amount of code that needs to be written when building a microservice or an aplication server.
Published on May 01, 2019

Example of using BSPump with CSV files
Let us say we have a CSV file, no, wait, a lot of CSV files that are coming to our storage directory with flashing speed. We even do not have the slightest notion what names of the files are, the only thing we know is that we need to process their data and deliver them to our database as quickly as possible.
Published on August 19, 2018
Building a private cloud on AMD Ryzen and Linux Containers
At our company, we develop our own software products that we offer to our clients and often also run ourselves. So far our company has operated its IT infrastructure — about 30 virtual servers—on a public cloud, specifically on MS Azure.
Published on July 01, 2018

Streaming Data from Various Sources
One of the main research and development topics nowadays is data processing and analysis, which can help companies discover relevant information about their customers or technologies using reports, visualizations, dashboards, and other business intelligence outputs.
Published on June 01, 2018

The Birth of Application Server Boilerplate
One of the most exciting tasks for our team in the last month was to create a new application server “boilerplate” that would be used as a basis for most of our growing data-processing products, as well as for other people and companies ...
Published on January 16, 2018

Binary distributions of OpenSSL static libraries
The official source of OpenSSL software is the OpenSSL website. One can download OpenSSL source codes archives and compile them for a given platform. The compilation work can sometimes be quite tedious, especially for exotic platforms. We, at TeskaLabs, set up this page because we frequently compile OpenSSL for various platforms for our internal purposes and this may save some time to other developers.
development
android
windows
ios
security
Published on July 20, 2017

Building High-Performance Application Servers - What You Need to Know
Using scalable and reliable software is vital for the success of any large-scale IT project. As increasing numbers of transactions are made, application infrastructure needs to stand strong and support that growth, and not be another source of problems.
Published on January 17, 2017
Key Areas and Best Practices to Focus for Mobile API Security
With APIs (Application Programming Interfaces) becoming a crucial factor in any web or mobile application, security feels more like a journey than a destination. Of all the constituents that encompass an application, API gateway offers easy access points for a hacker to break in and steal your data. A single error in API can cause immense problems for any organization using your API.
Published on November 22, 2016

5 Things to Look for in an Enterprise Mobile Development Platform Solution
Today many enteprises are looking to have their own mobile applications. With the right solution, you can build a mobile app that will fit your organization’s needs like a glove and be in the driver’s seat of the development.
Published on September 01, 2015

Why Developers Are Boosting Up Their Mobile Application Security?
Mobile application security is a significant issue for developers. Most try their best to make mobile apps secure and safe for their users. Here are some of the other reasons why developers are boosting up their mobile application security.
Published on April 14, 2015

Situations Where Mobile App Security Best Practices is Necessary
The use of mobile app security best practices has become a necessity as app development and mobile usage continue to grow. These practices are needed to improve consumer protection, trust, and regulatory compliance.
Published on March 24, 2015

SQL Injection - Are Developers to Blame for Data Security Breaches?
Of course, this is a bold statement, but for those who deal with security issues from mobile applications, they can pinpoint where the flaw occurred with developers not taking security into account when developing mobile apps. Security takes the back seat to app functionality and remains as second thought.
Published on March 07, 2015

The Golden Age of Black Hats
I experienced a precious moment, discovering the cause which contributed to today's dire state of mobile application security. App developers think that if their apps do not deal with money, they should not have to care about app security. Is it true?
Published on February 24, 2015
What's More Important For Mobile App Developers: Prioritizing Privacy, Security or Ease of Use?
The industry of mobile app development is rising quicker than the speed of light. However, the apps seem to have problems with security and privacy even though they are easy to use. Mobile apps are developed in a few months without regards to security, privacy, or the fact they can easily be breached by hackers. Some companies have known for months about a security issue, but don't do anything until there is a breach.
Published on February 17, 2015
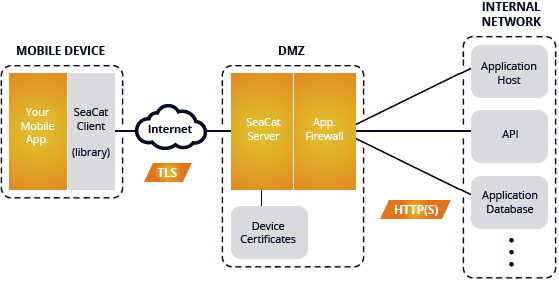
Software architect's point of view: Why use SeaCat
I've recently received an interesting question from one software architect: Why should he consider embedding SeaCat in his intended mobile application? This turned into a detailed discussion and I realised that not every benefit of SeaCat technology is apparent at first glance. Let me discuss the most common challenges of a software developer in the area of secure mobile communication and the way SeaCat helps to resolve them. The initial impulse for building SeaCat was actually out of frustration of repeating development challenges linked with implementation of secure mobile application communication. So let's talk about the most common challenges and how SeaCat address them.
Published on April 16, 2014