What's More Important For Mobile App Developers: Prioritizing Privacy, Security or Ease of Use?

The industry of mobile app development is rising quicker than the speed of light. However, the apps seem to have problems with security and privacy even though they are easy to use.
Mobile apps are developed in a few months without regards to security, privacy, or the fact they can easily be breached by hackers. Some companies have known for months about a security issue, but don't do anything until there is a breach.
According to an article on Forbes, Starbucks knew about a security issue (in their app) for months and didn't do anything about it until the app was breached. This was in January last year (2014), but with mobile apps being deployed at the rate of one per company per month, are they actually thinking about the security of the app before they deploy?
Security is an important part of a mobile app. Many people input their private information, passwords, and for some, even their bank information. The security on a mobile app can be breached if the company creating the app doesn’t work on securing the app before deployment.
Are you thinking about the security of the app before you deploy?
For those who create the mobile apps, some are pressured by top management to get the app out as fast as possible, however, top management doesn't seem to understand the faster a mobile app is deployed when it's not secure, will only bring down the app and possible, the company. It's hard for users to trust mobile apps again after a breach. Especially if the developers knew about the security flaw.
As the world becomes more mobile-centric, mobile apps are being used more. Are mobile app developers still building apps that are easy to use, with minimum security and less privacy for the users? If they are, there is an answer to the security issue.
Is the competition so fierce, a mobile app developer needs to pump out apps that allow hackers access to secure information? According to Domingo Guerra, president and co-founder of Appthority, mobile malware is on the rise. However, it still only applies to only .4 percent of mobile apps. The real threat is the "apps behavior, like aggressive data collection and data sharing, and how popular mobile apps downloaded to employee devices are handling sensitive company data."
Advertisers offer mobile app developers a kickback or what they call a push-back to include data collection that is not needed by the core functionality of the app. For example, a flashlight app uses geolocation and can access the mobile camera and their calendars. They add this functionality to monetize the app. This leaves the users open to data capturing and sharing.
The app may be free to download and use, but the user may find they are sharing information they know nothing about. This is a security issue some mobile app developers are ignoring at this time.
Differentiate yourself
To differentiate your mobile app from the competition is to offer the security and privacy users need to feel safe. SeaCat answers the call to adress and solve security concerning mobile applications, protecting user and business data and at the same time making the job easier for IT people.
Want to know how you can protect your mobile apps and senstive data correctly? Drop us a line atsupport@teskalabs.com and connect with us on Twitter @SeaCatMobi.
Most Recent Articles
You Might Be Interested in Reading These Articles

5 Things to Look for in an Enterprise Mobile Development Platform Solution
Today many enteprises are looking to have their own mobile applications. With the right solution, you can build a mobile app that will fit your organization’s needs like a glove and be in the driver’s seat of the development.
Published on September 01, 2015

Inotify in ASAB Library
From blocking read challenge, ctypes and bitmasks to a solution that enables the ASAB framework to react to changes in the file system in real time.
Published on August 15, 2023
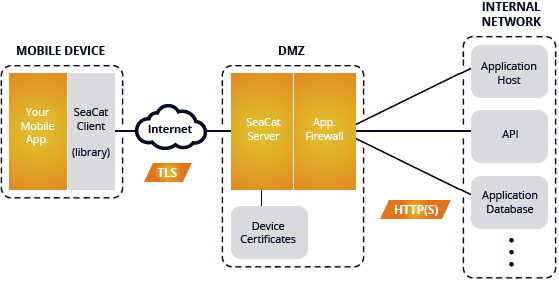
Software architect's point of view: Why use SeaCat
I've recently received an interesting question from one software architect: Why should he consider embedding SeaCat in his intended mobile application? This turned into a detailed discussion and I realised that not every benefit of SeaCat technology is apparent at first glance. Let me discuss the most common challenges of a software developer in the area of secure mobile communication and the way SeaCat helps to resolve them. The initial impulse for building SeaCat was actually out of frustration of repeating development challenges linked with implementation of secure mobile application communication. So let's talk about the most common challenges and how SeaCat address them.
Published on April 16, 2014