Cybersecurity - Data Privacy - IT Trends - Innovations

TeskaLabs helps LINET with cyber security compliance for medical devices
LINET is a major European manufacturer of hospital and nursing beds. The company´s portfolio includes solutions designed for intensive care, products for regular in-bed treatment, and also special beds for retirement homes and long-term care facilities.
Published on October 16, 2020

TeskaLabs and University hospital in Pilsen launches a pilot of zScanner - open source mobile app for medical photo documentation
zScanner is a mobile application for clinical and medical photo documentation. zScanner enables doctors and nurses to take photos of patient medical records, and of injuries of the patients, and upload them to a hospital information system. zScanner is an application created by the Institute of Clinical and Experimental Medicine in Prague (IKEM), a major Czech hospital, and the largest center of clinical and experimental medicine in the Czech Republic. During the pilot in the University hospital in Pilsen, zScanner is used at a Clinic of Oncology and Radiotherapy, and at the Clinic of anesthesiology, resuscitation and intensive medicine.
Published on September 17, 2020
Five Ways AI And Machine Learning Can Enhance Cybersecurity Strategy
Artificial Intelligence (AI) and its essential component machine learning are causing a stir in practically every industry from marketing to education. It’s no wonder designers and tech developers are finding ways to use the benefits of automated technologies to improve cybersecurity infrastructure and defend against increasingly complex and numerous cyber threats.
Published on June 24, 2020

Creative Dock, TeskaLabs, Indermedica, Czech Ministry of Industry and Trade and Line 1212 launch the indicative test for new COVID-19 coronavirus
🇨🇿 Uchránit přetížené zdravotníky před zbytečným náporem lidí i pomoci lidem, kteří mají obavy z nového typu koronaviru, ve správném vyhodnocení symptomů a dalším postupu má nový online Indikativní test Covid-19, který vyvinuly české technologické firmy spolu s ministerstvem průmyslu a obchodu a linkou 1212.
healthcare
data-privacy
covid19
Published on March 29, 2020

Cyber-health with a password and an antivirus program is not enough
At the beginning of December 2019, the operating system of the Benešov Hospital was crippled by a malicious computer virus to such an extent that no device could be started and doctors had to cancel all planned operations.
Published on February 14, 2020

TeskaLabs has become a leader of Mobile Healthcare applications in the Health (in) Future Platform
Cellphone instead of a filing cabinet. Until quite recently, doctors at the IKEM hospital in Prague needed to perform photo documentation by first taking pictures with a digital camera, and then downloading and/or uploading them via a computer network to patient cards. A solution to this tedious and time-consuming practice was made possible through the use of mobile scanning technology.
Published on December 10, 2019

zScanner: mobile app for medical photo documentation with security by TeskaLabs
zScanner is a mobile application for clinical and medical photo documentation. zScanner enables doctors to take photos of patient medical records, and of injuries of the patients, and upload them to a hospital information system. zScanner is an application developed and used by IKEM, a major Czech hospital, and the largest center of clinical and experimental medicine in the Czech Republic.
Published on May 12, 2019

IoT, AI and Cybersecurity Are Transforming Healthcare: Here's How
Technological advances are being made on a daily basis with one goal in mind - simplifying our daily lives. Everyone now owns a computer and smartphone and thanks to the Internet, everyone has access to lots of different types of information. The medical field has benefitted greatly from this advancement in technology. Not only does it help simplify many processes which would otherwise be long and tedious to complete, it also gives doctors and the medical personnel a powerful tool which allows them to do their jobs with more security.
medicat
healthcare
data-privacy
iot
Published on December 13, 2018

9 Ways To Improve Cybersecurity In Healthcare
Modern healthcare is deeply intertwined with technology. From the sophisticated machines used for diagnosing disease to the enterprise systems that store patient records, it is extremely difficult to run any healthcare organization today without heavily relying on information technology.
medicat
healthcare
data-privacy
Published on November 10, 2018

Developing a Mobile App in Healthcare
MediCat is one of TeskaLabs newest innovations and it centers around data protection and cybersecurity for the healthcare industry. In this article, we’ll explore the many use cases of MediCat.
medicat
data-privacy
healthcare
Published on October 15, 2018
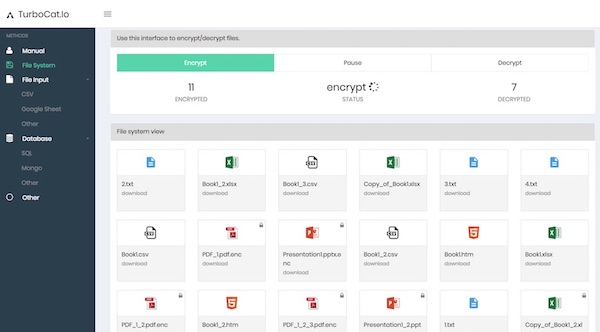
Customer interview: Read how Prodvinalco uses TurboCat.io for a file encryption
Data encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on September 13, 2018

Personal Data Deindetification: Pseudonymization
Pseudonymization is a critical part of GDPR compliance although there are no explicit GDPR pseudonymization requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on July 15, 2018

Personal Data Deindetification: Homomorphic encryption
Homomorphic encryption is a special type of encryption invented by IBM. Encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on June 14, 2018

Personal Data Deindetification: Data masking (or suppression)
Data masking (or suppression) represents the de fact standard of pseudonymisation. Pseudonymisation is a critical part of GDPR compliance although there are no explicit GDPR pseudonymisation requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on June 11, 2018

Personal Data Deindetification: Data Encryption
Data encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on May 16, 2018

Personal Data Deindetification: Anonymization
If you manage private data of any kind, you need to be familiar with the process of anonymization and how it can be used to keep the information you store safe from data breaches.
Published on April 16, 2018

Pseudonymization, Anonymization, Encryption ... what is the difference?
The year 2018 will, at least in Europe, be a turning point for data privacy and personal information protection. In this article, I will focus on personal data processing. I describe methods of de-identification of personal data, such as pseudonymization, anonymization, and encryption.
Published on November 28, 2017