Cybersecurity - Data Privacy - IT Trends - Innovations
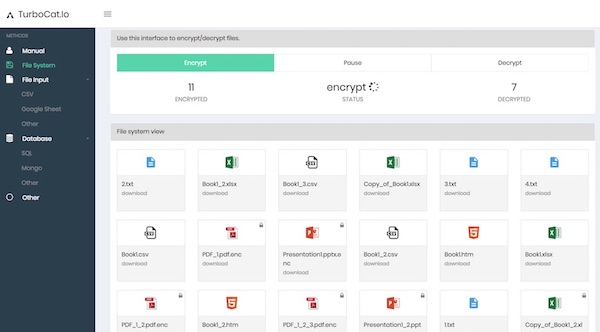
Customer interview: Read how Prodvinalco uses TurboCat.io for a file encryption
Data encryption is a critical part of GDPR compliance although there are no explicit GDPR encryption requirements. The regulation vaguely states that businesses must enforce safeguards and security measures to protect all consumer data that they handle. The GDPR refers to pseudonymization and encryption as “appropriate technical and organizational measures.
Published on September 13, 2018
Interview with Alex Goryachev, the Mastermind behind Cisco’s Grandest Innovation Challenge
We spoke to Alex Goryachev about the recent Innovate Everywhere Challenge, an initiative from Cisco to empower employees to think and act like passionate entrepreneurs with greater agility, speed, and risk-taking.
Published on August 16, 2016

Juggling A Corporate Job and A Side Business - Part 2
An interview with Mia Bennett, Head of Alliances and Special Projects, PwC, is a part of a series of interviews on enterprise innovation with corporate intrapreneurs, technology enthusiasts and visionaries within some of the world's largest companies.
Published on May 17, 2016

Create Unexpected Value to PwC and Expected Value to Startups - Part 1
An interview with Mia Bennett, Head of Alliances and Special Projects, PwC, is a part of a series of interviews on enterprise innovation with corporate intrapreneurs, technology enthusiasts and visionaries within some of the world's largest companies.
Published on April 25, 2016

What Does This Millennial Think About Innovation: An Interview with Matthew Bingley, Client Innovation Executive of Atos
Some people seem to be of the opinion that technological innovation has been largely iterative over the past 30 years and whilst we have achieve a great amount in terms of improving quality of life, there hasn’t been any real ‘ground shaking’ innovation. I suppose these same people are arguing that the internet is an iteration on interaction and isn’t particularly revolutionary.
Published on March 08, 2016

Security Architect Jiri Kohout: It's up to Us to Define How Secure The Internet Will Be
The security of connected applications, IoT, or mobile platforms, is based not only on secure development, but also on widespread knowledge about info security. Every user should have minimum knowledge about security. Every public tender should demand security of the final product or service.
Published on September 15, 2015

Security Researcher Filip Chytry: Online Security Is an Unattractive Topic - until People Get Hacked
I studied at Applied Cybernetics school and worked on various fields: robotics, networks and programming. There I got curious about security and became increasingly passionate about the industry, trying to learn more about cyber crime and attempting to hack into my classmates‘ computers for fun.
Published on August 20, 2015