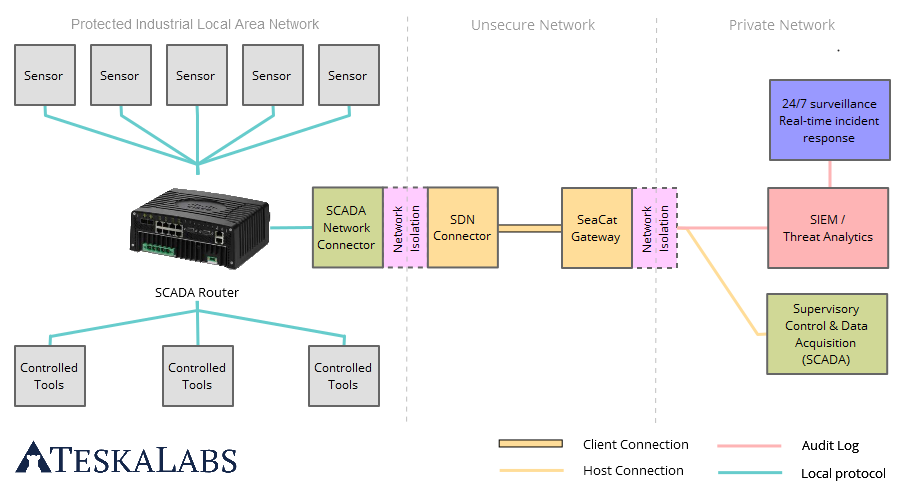
Prevent large-scale blackouts due to security breaches of SCADA systems
Attacks aimed at vulnerable SCADA systems – which we depend on to maintain national infrastructure and critical operations - could result in power grid failures or environmental disasters (like sewage and oil spills). Such attacks could also lead to destruction of physical assets, loss of data and more severely, human fatalities. A SCADA breach has the potential to negatively affect utility companies, as well as the economy as a whole, which are dependent on their services. Our technology isolates critical infrastructures and keeps them safe from illegal access, allowing utility companies to maintain communication and functionality to crucial Big Data databases and surveillance tracking systems. As a result, companies operate SCADA systems without worrying about intrusion to their production environment, effectively protecting SCADA systems from breaches.
Block unauthorized access and modification of critical data
Power plants, factories, gas stations, and other industrial facilities require input data from controllers, sensors, and/or drivers to make production-based choices, which keeps things flowing. If such data is corrupted or altered, these processes may fail, interrupting production entirely. Our technology keeps the data source protected, and deters any effort to change the communication, or attempts to communicate from untrusted systems and devices, ensuring the integrity, confidentiality, and accessibility of important information.
Compliant with industry regulations and security standards
SCADA systems control vital processes and physical assets that provide key resources like water, electric power, gas and oil. As such, SCADA systems warrant appropriate security measures that meet industry requirements and rigorous security standards. To comply with all standards and regulations requires a consistent security process and implementation throughout the whole company. Our technology offers by-the-book security standards concerning data-in-motion protection, authentication, public key infrastructure and more to help utility companies adhere to mandatory security requirements.
Minimize the impact of a security breach
Utility companies need to run SCADA systems in a reliable and secure manner and can’t afford to allow attacks from happening. Without 24/7 monitoring, it is not feasible to identify potential threats, monitor suspicious activity, and swiftly respond to cyber attacks. Our technology gives system operators and administrators the ability to detect threats, track system-related activities, and isolate security incidents. Further, our professional team also monitor these systems remotely, and gives real-time and precise incident responses to all issues. With a dependable incident response service and security monitoring system in place, utility companies take comfort in knowing they can manage complicated networks of important SCADA-controlled physical machines and SCADA systems safely.