OpenSSL emergency release impact analysis re TeskaLabs’ SeaCat
Tue May 3 2016
We help you to operate your mobile app(s) securely. You might have noticed that OpenSSL has recently announced an emergency release because they identified a series of security defects, rated with maximum severity "High." The version of fixed OpenSSL is 1.0.2h, released on 3rd May 2016.
OpenSSL is a widely used cryptographic library in server products, and you very likely operate many such servers.
Our mission is to keep you safe from any harm linked with the mobile app we protect. We take this very seriously and for that reason, we follow up with an analysis of the impact on mobile apps protected by SeaCat.
EBCDIC overread (CVE-2016-2176)
NO. SeaCat-enabled mobile app is not at risk.
Padding Oracle in AES-NI CBC MAC check (CVE-2016-2107)
YES. There is an impact on the SeaCat Gateway, and the issue has been fixed in the newest release v1603-1. This issue affects the AES encryption used for data transfer between the client and the server. Asymmetric encryption is slow. Thus, it is used only for exchanging the master key. The master key is randomly calculated to encrypt data in a symmetric way. The people capture the data packets and modify them can reveal the encrypted data.
There is no publicly available exploit, so the attacker must have in-depth knowledge and programming skills to exploit this vulnerability. For SeaCat Gateways managed by TeskaLabs, you don’t need to do anything. We took care of the deployment, and the Gateways have been updated. If you manage the SeaCat Gateways on your own, our technical team will coordinate the upgrade with you.
This issue affect all OpenSSL-based servers. If you are not sure whether mentioned issues affect your infrastructure, you can do a test. The test is downloadable from Github.
ASN.1 BIO excessive memory allocation (CVE-2016-2109)
NO. SeaCat-enabled mobile app is not at risk.
Memory corruption in the ASN.1 encoder (CVE-2016-2108)
NO. SeaCat-enabled mobile app is not at risk.
EVP_EncryptUpdate overflow (CVE-2016-2106)
NO. SeaCat-enabled mobile app is not at risk.
EVP_EncodeUpdate overflow (CVE-2016-2105)
NO. SeaCat-enabled mobile app is not at risk.
TeskaLabs product versions with OpenSSL 1.0.2h security fixes
- SeaCat Gateway v1603-rc.1
- SeaCat Client for Android v1601-1
Impact on other OpenSSL-based solutions
OpenSSL is widely used in other software products such as HTTP Apache server and others. The current security OpenSSL release fixes an exploitable vulnerability, and if you don’t update, your data security can be compromised. Please make sure that you quickly update all of your impacted business-critical systems or systems that transfer highly-sensitive data. If updating is not a viable option for you, please consider performing a shutdown of those services. We are of course ready to help you.
Next steps
We will be coordinating with you individually if needed, and if have any question or concern, please contact support@teskalabs.com or just hit 'reply'.
Most Recent Articles
You Might Be Interested in Reading These Articles
SeaCat Application Security Technology Is Not Impacted by the SWEET32 Issue (CVE-2016-2183)
The new vulnerability CVE-2016-2183 affects the 3DES block cipher in TLS and OpenVPN software. During an attack, attackers need to find a collision of block cipher initialization vector used at the beginning of the encrypted data stream and decrypt the traffic between the victim and the server.
Published on August 26, 2016
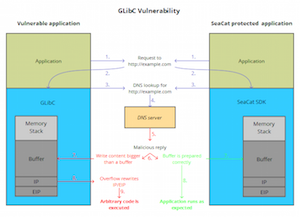
TeskaLabs’ Technology SeaCat Unaffected by GNU C Library Security Vulnerability (CVE-2015-7547)
TeskaLabs, a Prague and London based startup in application security, today affirmed that their core products are not exposed to the GLibC flaw, a highly critical security vulnerability. There is now a rapidly growing number of IoT devices that use Linux as their operating system and inherently GLibC.
Published on February 17, 2016

OpenSSL DROWN Vulnerability Affects Millions of HTTPS Websites and Software Supporting SSLv2 (CVE-2016-0800)
DROWN is caused by legacy OpenSSL SSLv2 protocol, known to have many deficiencies. Security experts have recommended to turn it off, but apparently many servers still support it because disabling SSLv2 requires non-default reconfiguration of the SSL cryptographic settings which is not easy for common IT people who have limited security knowledge and don’t know the location to disable this protocol and the way to disable it.
Published on April 12, 2016