SeaCat Technology and the Latest OpenSSL Update (1.1.0d, 1.0.2k)
Thursday, January 26, 2017
OpenSSL released a new version on 26 January 2017. The new release fixed one low-severity issue and three moderate ones:
- Truncated packet could crash via OOB read (CVE-2017-3731)
- Bad (EC)DHE parameters cause a client crash (CVE-2017-3730)
- BN_mod_exp may produce incorrect results on x86_64 (CVE-2017-3732)
- Montgomery multiplication may produce incorrect results (CVE-2016-7055)
Except for the (EC)DHE parameter-related issue, all mentioned issues relates to functionalities that are never used by SeaCat technology. An attack based CVE-2017-3730 affects only the client side of the communication. A successful attack results in a client crash during the beginning of a negotiation process. Attackers have to have the data communication under control to be able to send specially crafted packets.
Recommendation:
We recommend you to update to the latest version of SeaCat client. If you have any question, please contact support@teskalabs.com. Alternatively, look at our documentation to know more about SeaCat application security technology.
Most Recent Articles
You Might Be Interested in Reading These Articles
SeaCat Technology and the Latest OpenSSL Update (1.1.0e)
We help you to operate your mobile and IoT apps securely. You may have noticed that OpenSSL released a new version on February 16, 2017. The new version fixed one high-severity issue regarding renegotiation of the Encrypt-then-MAC (EtM) extension.
Published on February 21, 2017
OpenSSL emergency release impact analysis re TeskaLabs' SeaCat
We help you to operate your mobile app(s) securely. You might have noticed that OpenSSL has recently announced an emergency release because they identified a series of security defects, rated with maximum severity High. The version of fixed OpenSSL is 1.0.2h, released on 3rd May 2016.
Published on May 04, 2016
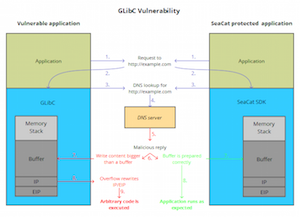
TeskaLabs’ Technology SeaCat Unaffected by GNU C Library Security Vulnerability (CVE-2015-7547)
TeskaLabs, a Prague and London based startup in application security, today affirmed that their core products are not exposed to the GLibC flaw, a highly critical security vulnerability. There is now a rapidly growing number of IoT devices that use Linux as their operating system and inherently GLibC.
Published on February 17, 2016